CCleaner, a Windows utility app was recently found to be carrying malware through a backdoor. The attack seems to be have been much more targeted and sophisticated than depicted previously. Research have been digging through data seized command and control center, and found a lot of evidence that the attackers were using this method to target world’s biggest tech companies.
New information posted by Avast and Cisco’s Talos research group, first reported by Wired, gives us more details. When the server was seized, the attackers were targeting a strong of internal domains with a second-stage payload. This payload was designed to collect data and provide continued access to any infected device.
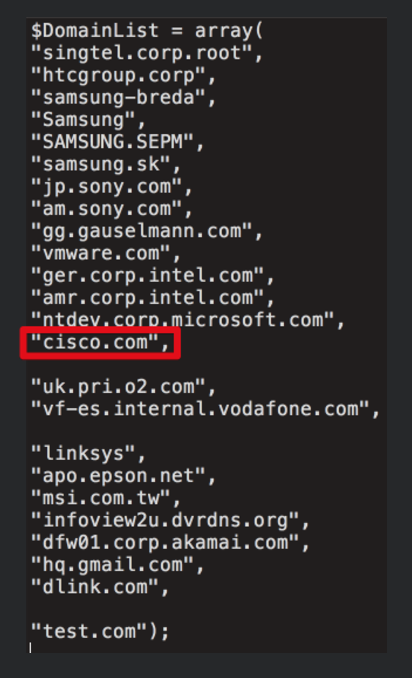
Published by Talos, we get a list of domains that gives us insight into targeted major tech companies. For example, “Ntdev.corp.microsoft.com” is an internal domain for Windows developers. Then there’s hq.gmail.com that appears to be the internal Gmail access point for Google employees. Other companies include Samsung, Sony, Intel, and Akamai.
It’s unclear how compromised some of these companies are. Talos said that at least 20 computers that were targeted by the payload, but researchers did not disclose which companies were involved. Kaspersky Researchers have found significant code overlap between CCleaner attack and previous attacks by the Axiom threat group.
We will continue to keep you updated as more information comes in.





